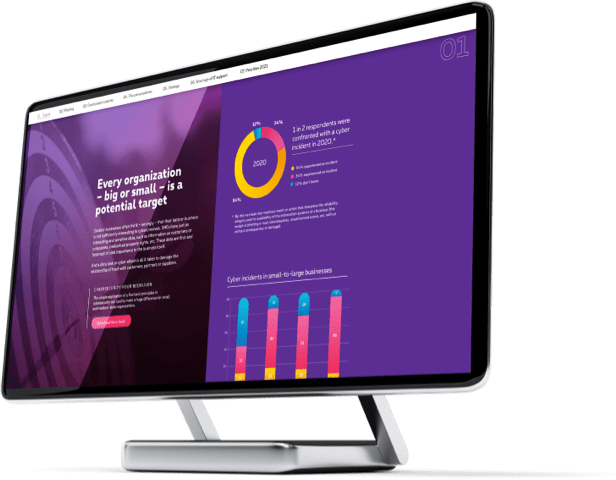
Digitalization increases cyber risks. Phishing is the most common type of cyber attack today. Are Belgian and Dutch businesses adequately prepared? Together with Proximus SpearIT, Davinsi Labs and Telindus Netherlands, Proximus carried out some research in this area among its customers.
CYBERSECURITY
deal with cyber threats?
How do companies


Any business – large or small – is a potential target
1


3 cybersecurity priorities for 2021
6


There is a shortage of IT support
5


50% of organizations have no security strategy
4


Phishing is the most commonly occurring attack
7


An incident is not always picked up
2


The impact of an incident is greater than expected
3

7 conclusions from the research

You can perform a number of checks to identify a phishing attempt:
1. Does the e-mail contain spelling mistakes, poor grammar, or other obvious errors? Bear in mind, however, that fraudsters are getting better all the time.
2. Does the domain name of the sender’s e-mail address differ from the real domain name of the company that is sending the e-mail? You can check this in the source code of the mail. And by hovering over a link you can check whether the URL of the link in the mail is different from the real domain name of the company.
3. Fraudsters try to creare a sense of urgency. If you are asked to do something urgently or quickly (often just before the weekend or a public holiday), be on your guard.
4. Phishing e-mails are often not addressed to you personally because the fraudsters don’t know your name.
Recognizing phishing

There are three ways to prevent phishing:
1. Making people aware is the first and most important line of defense where phishing is concerned. Cybersecurity awareness among staff members can be significantly increased by conducting regular simulated phishing campaigns.
2. Secure incoming traffic with traditional filters such as anti-spam and filter communication tools for incoming messages.
3. Secure outgoing traffic by, for example, scanning URLs or the content of outgoing messages.
Preventing phishing

When you click on a link in a phishing mail, the damage needs to be minimized as quickly as possible by:
1. Blocking or resetting accounts and changing your passwords.
2. Immediately checking logfiles to see whether there has been an attack, and whether any other phishing messages have come in. This information is useful for monitoring data on new attacks. There may be a larger-scale phishing campaign being directed at your company. There have been cases where the HR department has been contacted, supposedly by members of staff, and asked to change bank account numbers for salary payments.
3. Tighten up prevention measures with the results of a survey, for example by blocking the domain names associated with the attack.
Clicked. What now?
“All SNCB applications run on the device from inside a shielded container, in order to have a secure, high-performance device.”
Phishing is the most commonly occurring attack. Cybercriminals try to trick your personnel into going to rogue websites and leaving personal information there. They misuse that information to empty bank accounts. What can you do about it?
How to recognize and avoid phishing?
Started his career at SNCB as a train conductor in 1998. Since then, he has held a variety of jobs but has been active as the ICT Coordinator since 2017.
Pascal Rooms

Proximus supplies SNCB with tools to manage 26,000 mobile devices
SNCB will soon own a fleet of 26,000 mobile devices for the SNCB train conductors, train drivers, station personnel, and security staff. Proximus is providing the hardware and Mobile Device Management (MDM) solution for the smartphones, tablets, and smartwatches.
To manage and secure its fleet of devices, SNCB integrates its MDM platform, Microsoft Intune with the Samsung KNOX on the Azure cloud platform. One of the things Proximus is responsible for is to ensure that employees locate the right apps, tailored to their job specifications. All SNCB applications run on the device from inside a shielded container, so that employees have access to a secure, high-performance device.

Read the full interview

Digitalization increases cyber risks. Phishing is the most common type of cyber attack today. Are Belgian and Dutch businesses adequately prepared? Together with Proximus SpearIT, Davinsi Labs and Telindus Netherlands, Proximus carried out some research in this area among its customers.
deal with
cyber threats?
CYBERSECURITY
How do companies
7 conclusions from the research

Any business – large or small – is a potential target
1


An incident is not always picked up
2


The impact of an incident is greater than expected
3


50% of organizations have no security strategy
4


There is a shortage of IT support
5


3 cybersecurity priorities for 2021
6


Phishing is the most commonly occurring attack
7


You can perform a number of checks to identify a phishing attempt:
1. Does the e-mail contain spelling mistakes, poor grammar, or other obvious errors? Bear in mind, however, that fraudsters are getting better all the time.
2. Does the domain name of the sender’s e-mail address differ from the real domain name of the company that is sending the e-mail? You can check this in the source code of the mail. And by hovering over a link you can check whether the URL of the link in the mail is different from the real domain name of the company.
3. Fraudsters try to creare a sense of urgency. If you are asked to do something urgently or quickly (often just before the weekend or a public holiday), be on your guard.
4. Phishing e-mails are often not addressed to you personally because the fraudsters don’t know your name.
Recognizing phishing

There are three ways to prevent phishing:
1. Making people aware is the first and most important line of defense where phishing is concerned. Cybersecurity awareness among staff members can be significantly increased by conducting regular simulated phishing campaigns.
2. Secure incoming traffic with traditional filters such as anti-spam and filter communication tools for incoming messages.
3. Secure outgoing traffic by, for example, scanning URLs or the content of outgoing messages.
Preventing phishing

When you click on a link in a phishing mail, the damage needs to be minimized as quickly as possible by:
1. Blocking or resetting accounts and changing your passwords.
2. Immediately checking logfiles to see whether there has been an attack, and whether any other phishing messages have come in. This information is useful for monitoring data on new attacks. There may be a larger-scale phishing campaign being directed at your company. There have been cases where the HR department has been contacted, supposedly by members of staff, and asked to change bank account numbers for salary payments.
3. Tighten up prevention measures with the results of a survey, for example by blocking the domain names associated with the attack.
Clicked. What now?
“All SNCB applications run on the device from inside a shielded container, in order to have a secure, high-performance device.”
Started his career at SNCB as a train conductor in 1998. Since then, he has held a variety of jobs but has been active as the ICT Coordinator since 2017.
Pascal Rooms

How to recognize and avoid phishing?
Phishing is the most commonly occurring attack. Cybercriminals try to trick your personnel into going to rogue websites and leaving personal information there. They misuse that information to empty bank accounts. What can you do about it?
Proximus supplies SNCB with tools to manage 26,000 mobile devices
SNCB will soon own a fleet of 26,000 mobile devices for the SNCB train conductors, train drivers, station personnel, and security staff. Proximus is providing the hardware and Mobile Device Management (MDM) solution for the smartphones, tablets, and smartwatches.
To manage and secure its fleet of devices, SNCB integrates its MDM platform, Microsoft Intune with the Samsung KNOX on the Azure cloud platform. One of the things Proximus is responsible for is to ensure that employees locate the right apps, tailored to their job specifications. All SNCB applications run on the device from inside a shielded container, so that employees have access to a secure, high-performance device.

Read the full interview